A group of researchers found images on Docker Hub that turned out to contain a hidden cryptocurrency mining code, according to Palo Alto Network’s Unit 42. The images were uploaded to the legitimate repository of Docker Hub, so let’s find out more in Monero latest news today.
Unit 42 researchers found images and now they identified six variants of the Docker Image that contained the XMRig cryptominer which allowed hackers to mine Monero from a compromised Docker container. The images were hosted in an account on the official Docker Hub repository which was downloaded more than 2 million times. One of the crypto wallets associated with the hackers contained more than 525 Monero virtual coins worth about $36,000 according to the report.
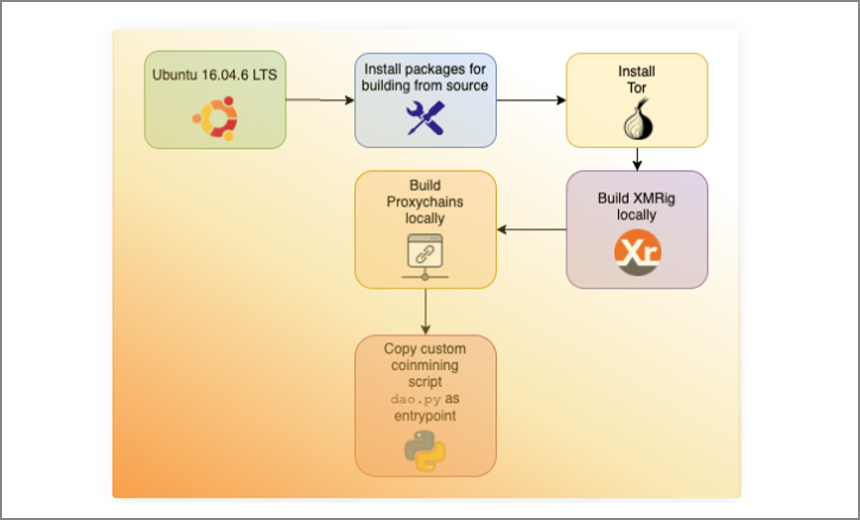
While it is still unclear who is behind the scheme, Unit 42 researchers found that the malicious account was created back in 2019 and was used to distribute the images. Docker took down the account after it was notified by Unit 43. Docker is a popular platform as a service offering for Windows and Linux devices that developers used to help develop applications:
“Docker containers provide a convenient way for packaging software, which is evident by its increasing adoption rate… This makes it easy for a malicious actor to distribute their [malicious] images to any machine that supports Docker and start using its computing resources toward cryptojacking.”
The campaign is now inactive but the researchers warned that the attackers can continue soon with their activities by setting up other accounts. The malicious images were built using a custom mining code loaded once the victims open the images. Hackers hosted the images in a Docker Hub repository which was similar to the Microsoft Azure packages in order to trick the victims into downloading:
“All the images here have a version of a custom Python script that starts the coin mining process using network anonymizing tools like Tor and ProxyChains. This script is registered as the entry point for the images so that as soon as the image is launched, the script and thus coin mining starts.”
The hackers also used the Tor browser and Proxchains-open-source software which allowed users to run the programs through a proxy server, as Chitwadgi noted:
“A firewall sitting between the victim miner and the internet would only see encrypted Tor traffic instead of the coin mining traffic that could trigger a different security team response compared to cleartext coin mining activity.”
DC Forecasts is a leader in many crypto news categories, striving for the highest journalistic standards and abiding by a strict set of editorial policies. If you are interested to offer your expertise or contribute to our news website, feel free to contact us at [email protected]






















Discussion about this post