The Cybersecurity firm ESET from Slovakia reported success in disrupting the operating monero-mining Botnet in Latin America as we are reading further in the Monero news.
The Slovakian cybersecurity firm ESET announced earlier today (April 23, 2020) that the malware successfully infected more than 35,000 computers since May 2019 and most of the devices were located in Peru. The ESET researchers named the botnet VictoryGate and noted that the main activity was illicit mining of monero or better known as cryptojacking.
Cryptojacking is a term in the crypto industry that defines crypto-mining attacks that function by installing malware that uses the computers’ processing power and mines cryptocurrencies without the owners’ approval or knowledge. The company’s announcement noted that the malware resulted in high resource usage in the infected computers and resulted in sustained 90-99% CPU load which can lead to overheating and eventually damaging the device.
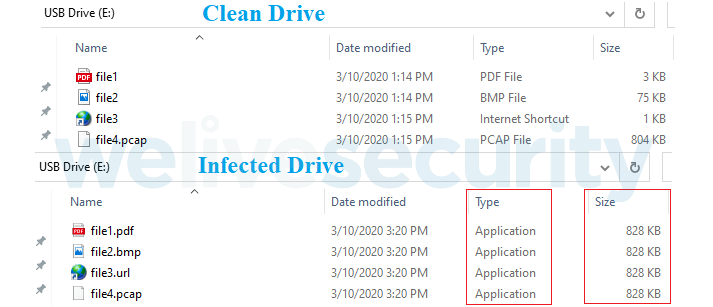
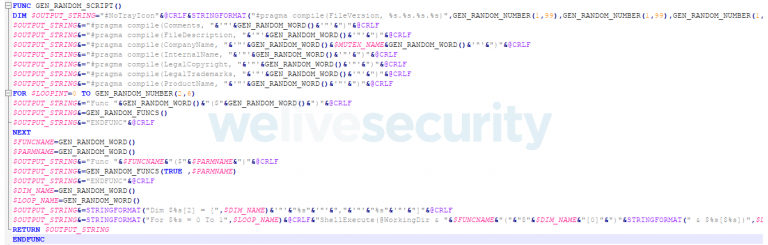
The botnet had a propagation vector that used external USB drives that seem to have files with names and icons which were the same as the ones contained originally. ESET wrote:
“However, the original files have been copied to a hidden directory in the root of the drive and Windows executables have been provided as apparent namesakes.’’
By detecting the botnet ESET had some success in disrupting the operations by taking down the command and control server. This works by setting up a sinkhole and diverts the requests to alternative domain names which allowed ESET to monitor and have full control over the infected hosts. ESET was working with Shadowserver Foundation when trying to mitigate the threat by VictoryGate:
“Despite our efforts, infected USB drives will continue to circulate and new infections will still occur. The main difference is that the bots will no longer receive commands from the C&C […] However, those PCs that were infected prior to the disruption may continue to perform crypto mining on behalf of the botmaster.”
The users can use the company’s online scanner for free in the meantime if they believe that the devices have been infected by the botnet. As per the reports in our XMR news, the attackers behind ‘’Sodinokibi’’ ransomware switched to Monero and ditched Bitcoin to better protect their identities.
DC Forecasts is a leader in many crypto news categories, striving for the highest journalistic standards and abiding by a strict set of editorial policies. If you are interested to offer your expertise or contribute to our news website, feel free to contact us at [email protected]




















Discussion about this post