Dogecoin’s use cases are starting to change nowadays after the TikTok boom as hackers are using it to conduct malicious activities according to reports that we have in our latest Dogecoin news.
Dogecoin’s use cases evolved over time as the coin was initially created as a joke in 2014, then became one of the most desired cryptocurrencies in 2015, it also became Elon Musk’s favorite in 2018 and as of latest, a TikTok sensation. Things however took a darker turn as the hackers started utilizing it to control crypto mining botnets according to the report by the security firm Intezer Labs.
Undetected Doki attack actively infecting vulnerable #Docker servers in the cloud. Attacker uses a novel Domain Generation Algorithm (DGA) based on a DogeCoin digital wallet to generate C&C domains. Research by @NicoleFishi19 and @kajilot https://t.co/CS1aK5DXjv
— Intezer (@IntezerLabs) July 28, 2020
Intezer Labs, a New York-based malware analysis company found out that hackers started using the infamous “Doki” backdoor which was using Dogecoin wallets to mask their online presence. The company said they were analyzing Doki, the Trojan Virus since 2020 but they recently discovered its use in installing crypto-mining malware later. The hacker under the name NGrok uncovered a new method to use Dogecoin wallets for infiltrating the web servers according to the company. The usage is a first of its kind which was initially used for funnier purposes.
Intezer Labs found out that Doki was using an undocumented method to contact the operators by abusing the DOGE blockchain in a way to generate control and command domain addresses. Using Dogecoin transactions allowed the attackers to change these addresses on affected servers and computers that ran the NgrokMonero mining bots. By doing so, hackers were able to hide their location and prevented detection:
“While some malware strains connect to raw IP addresses or hardcoded URLs included in their source code, Doki used a dynamic algorithm to determine the control and command (C&C) address using the Dogecoin API.”
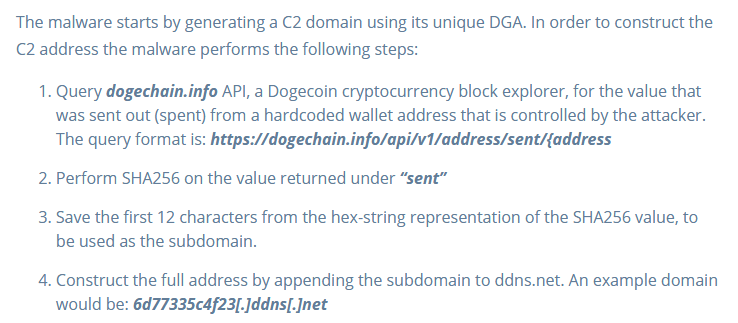
The company added that these steps meant security companies have to access the hackers’ dogecoin wallet in order to take down Doki which was quite impossible without knowing the wallet’s private keys. Using Doki allowed Ngrok to control the newly-deployed Alpine Linux servers for running the crypto-mining operations as they used the Doki service to determine the URL of the control and command server. Intezer researchers studied the process and detailed the steps in their report.
Intezer has discovered a new strain of Linux malware this week.
The new Doki backdoor is something very interesting as it uses the Dogecoin API to compute its C&C server addresseshttps://t.co/8pnSQ2dp7g pic.twitter.com/547TprDYwq
— Catalin Cimpanu (@campuscodi) July 28, 2020
This was a part of a bigger attack as the NGrok gang gained access to command servers as they deployed another botnet to mine XMR. Dogecoin served as an access bridge as ZDNet researcher Catalin Cimpanu said:
“Doki has been active since this January, but remained undetected on all 60 “VirusTotal” scanning software used on Linux servers.”
DC Forecasts is a leader in many crypto news categories, striving for the highest journalistic standards and abiding by a strict set of editorial policies. If you are interested to offer your expertise or contribute to our news website, feel free to contact us at editor@dcforecasts.com





















Discussion about this post